Responsive Analytics - the key to a quick incident response is an instant access to historical data. A responsive and intuitive analytics interface allows for complex investigations and a quick outcome. Any enhanced search or complex summary is automatically saved as a template, so you can be even quicker next time.
Unique Aggregation - through a unique technology billions of information records can be reduced to just a few relevant aggregated ones, which are presented in near real-time and enable for further drill down.
Hierarchical Multi-Tenant Storage - you can keep the costs low and performance high through a smart usage of the different storage technologies. Indexes can be kept on an SSD for 6 months and moved to a RAID later, the Raw Data can be stored on a SAN and later be moved to a NAS, the Summaries can be stored partly on SSD and partly on a SAN or all can be stored on your hard disk. Although you can spread your data over different storage technologies this is transparent to the frontend.
Data and Index Compression - why to use up to 10 or maybe 20 times more storage space than you really need? With SEQREL's logXtender all Data, Indexes, Summaries or the cached Search Results are compressed as they come.

Plugin Free - the dilemma was for a long time whether to update a software when needed or when a new vendor plugin becomes available. Through a unique technology this is no longer a concern, as all plugins are built dynamically and any change in the log structure would be detected on the fly. The system just needs to know how an IP Address or the CEF header looks like, which is probably already supported by the time you read this.
Taxonomy Detection - how would you know what a log type you see, when you see it for the first time in a log file? Probably you would recognize some keywords like "User", "Accept", "Deny", "Virus" or more complex constructions like "logged in" or "login failed". LogXtender can do the same and so enhance the classic and sometimes too inconsistent and limited lookup-table approach of mapping a vendor Event ID to some event Category and Sub-Category values.
Field Detection - you can give the system one or more known user IDs and the system will find the rest for you. You can start by looking for usernames like root, admin or Administrator and maybe add some of those used in Brute Force Attacks. Shall any classic approach like looking for "username=root" or "User admin" fail, you would still have a reliable user detection and maybe detect a threat you would not detect with classical methods.

Data Pseudonymization and Anonymization - compliance or company internal regulations or data privacy concerns might require that data access is only allowed on a need to know basis. Maybe some data shall first be visible after an approval is requested and the data access is granted. This might become a real concern once data sources providing critical information needed for threat detection cannot be connected. To help you overcome such issues, whether during the project implementation or during later operations, SEQREL's logXtender offers enhanced Role Based Data Protection, where specific Roles can get custom Data Access permissions. A Role can get more rights than the system default for a specific Field, while another Role might be granted less permissions for the same Field (e.g. User or the Source IP)
Pseudonymized Analytics - a user with less Data Access Permissions will still be able to run investigations, as a Pseudonym will be consistent throughout the data. A role based approval workflow is available, shall a threat be detected and the real data behind the Pseudonym be needed.

Adaptive Parsing,
Taxonomy Detection,
Adaptive Aggregation,
Role Based Data Privacy,
Complex Data Analytics,
Threat Intelligence Integration,
Enhanced Enrichment,
Data Privacy Workflow,
Multi-Tenant, Cloud-Ready Architecture,
Granular Role Based Access Control,
Customizable User Interface,
Collaborative Incident Response,
Multi-Threaded,
One-Click Data Analytics Dashboards,
Data Drilldown

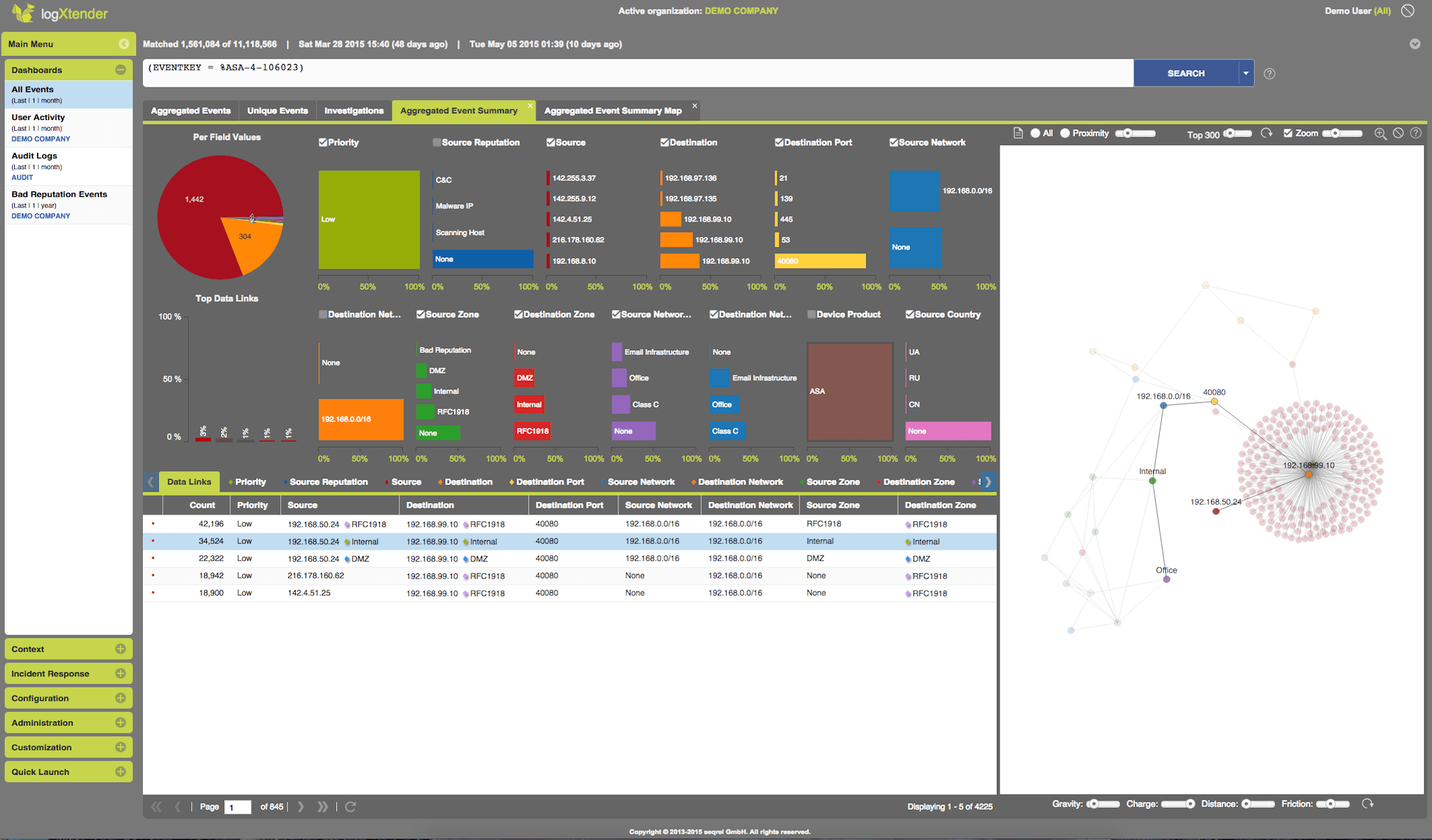
Complex Data Analytics

Threat Intelligence Integration
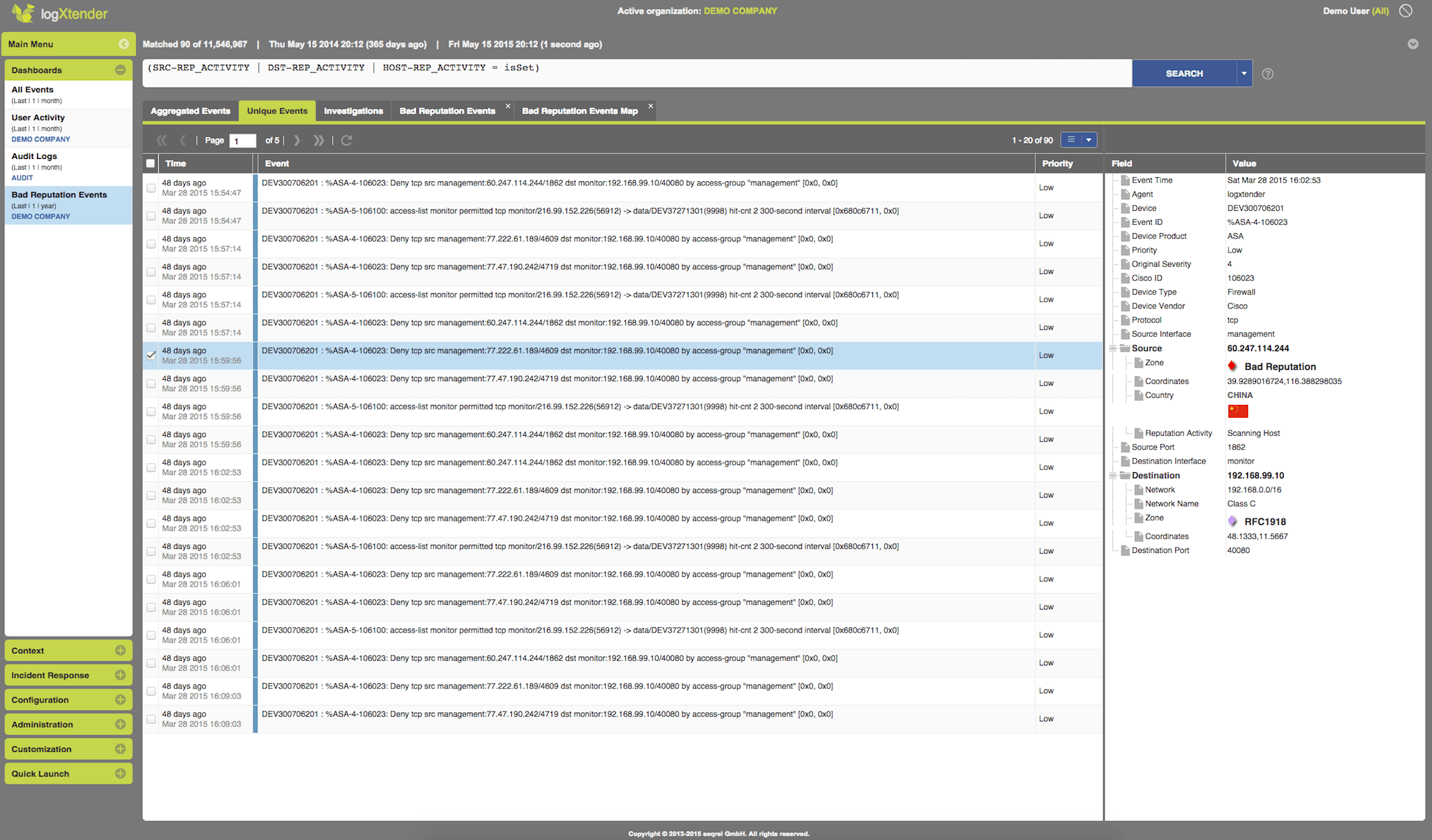
Enhanced Event Enrichment
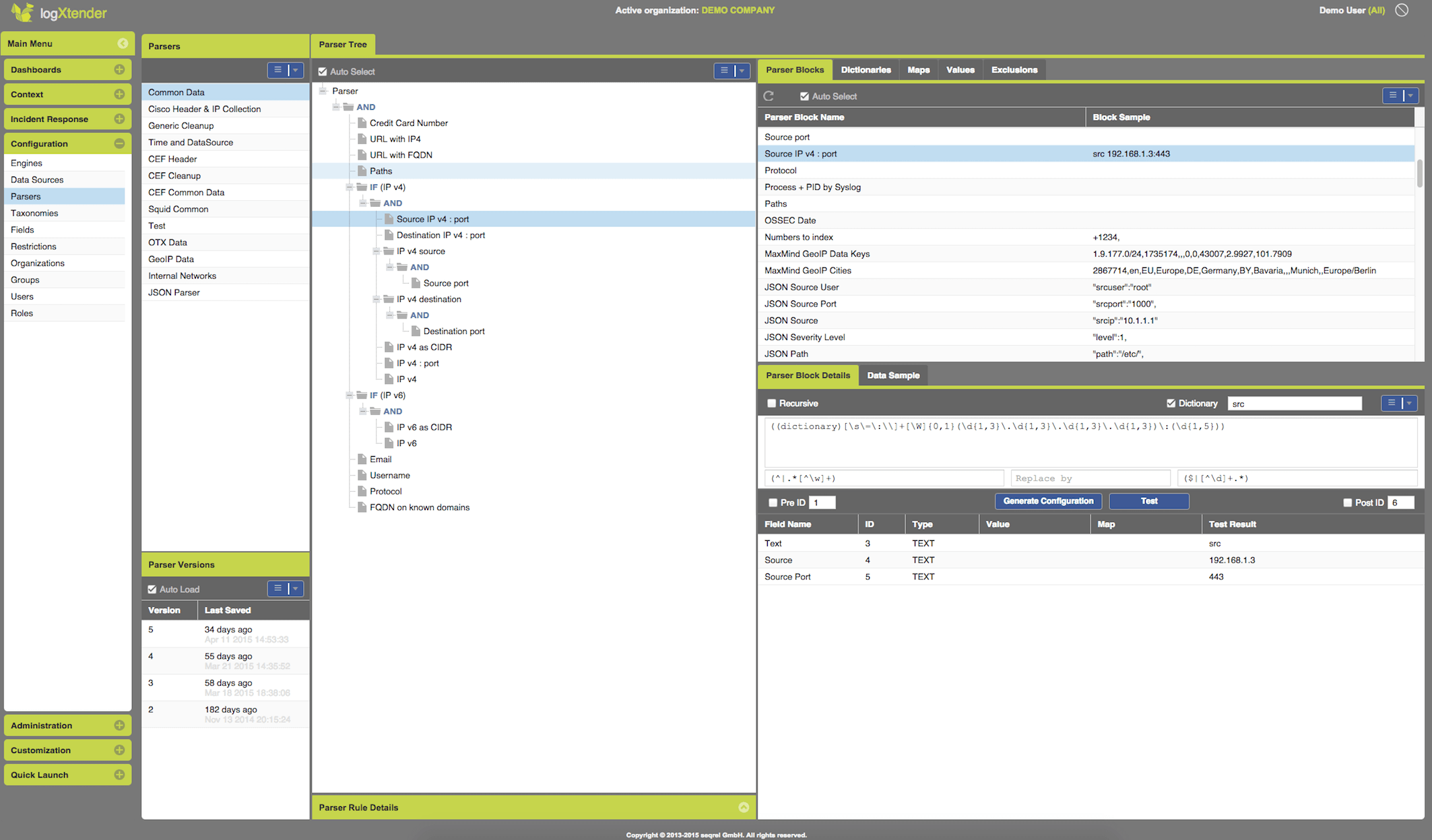
Plugin-Free Adaptive Parsing
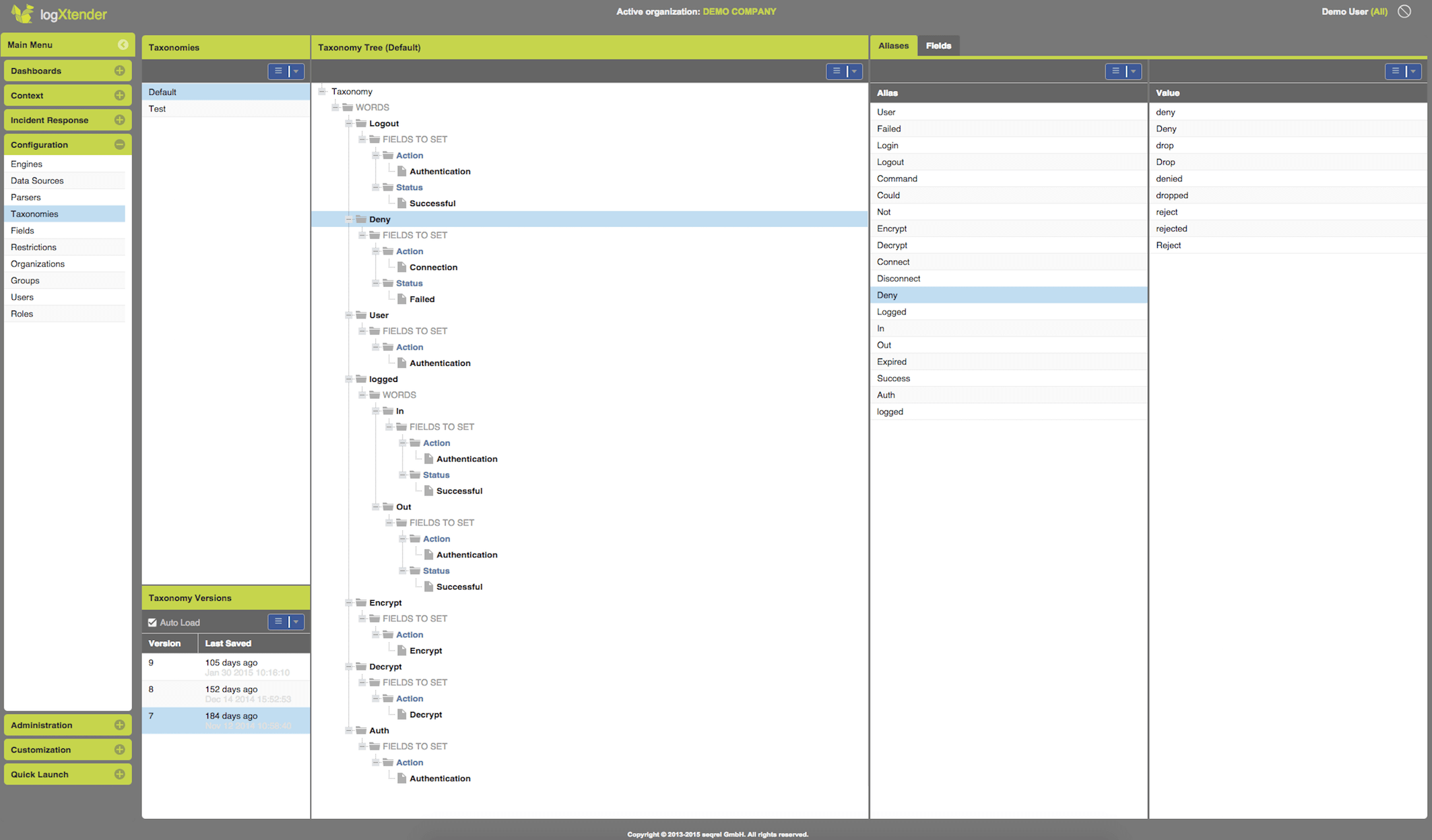
Event Taxonomy Detection
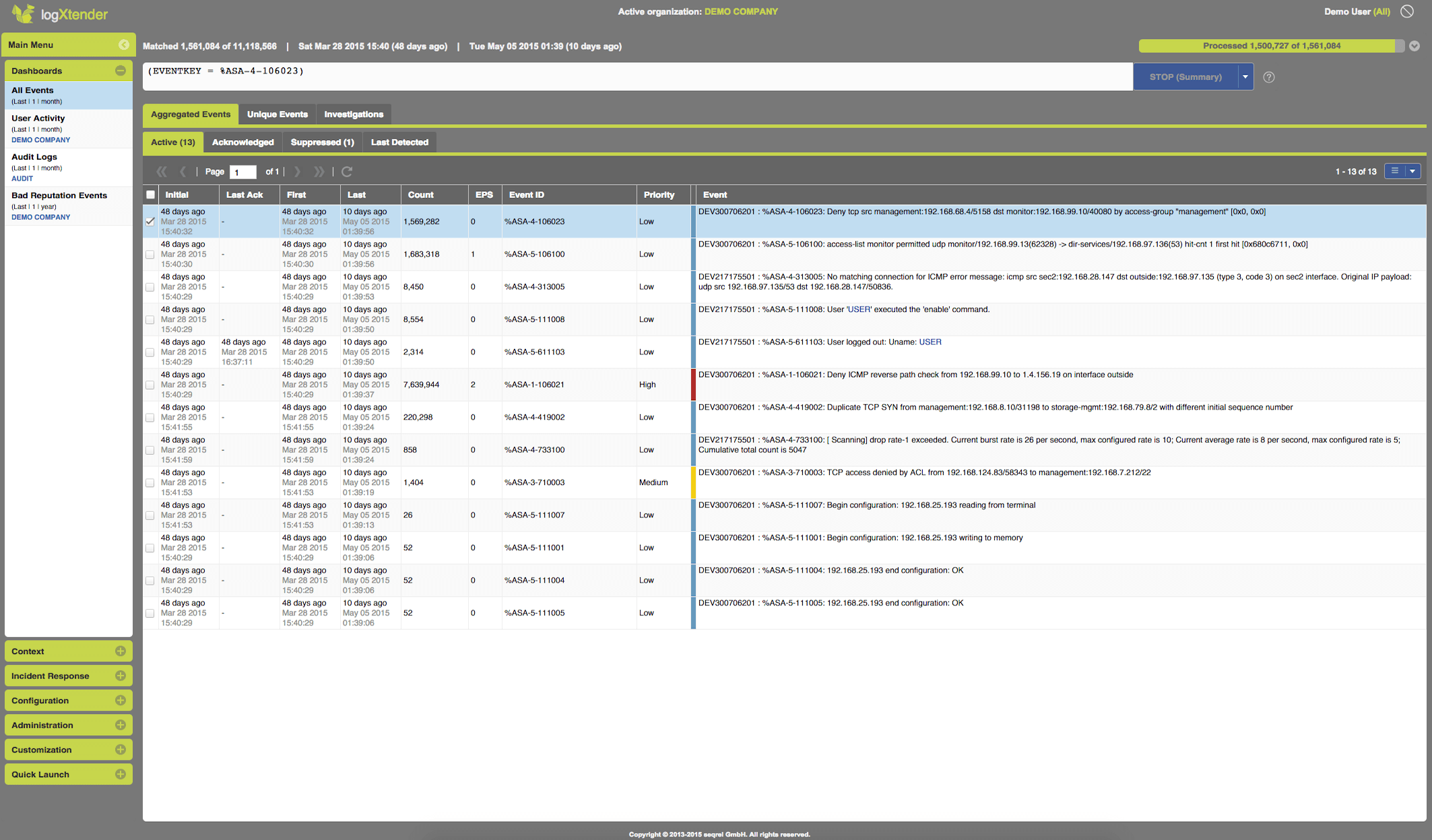
Adaptive Event Aggregation
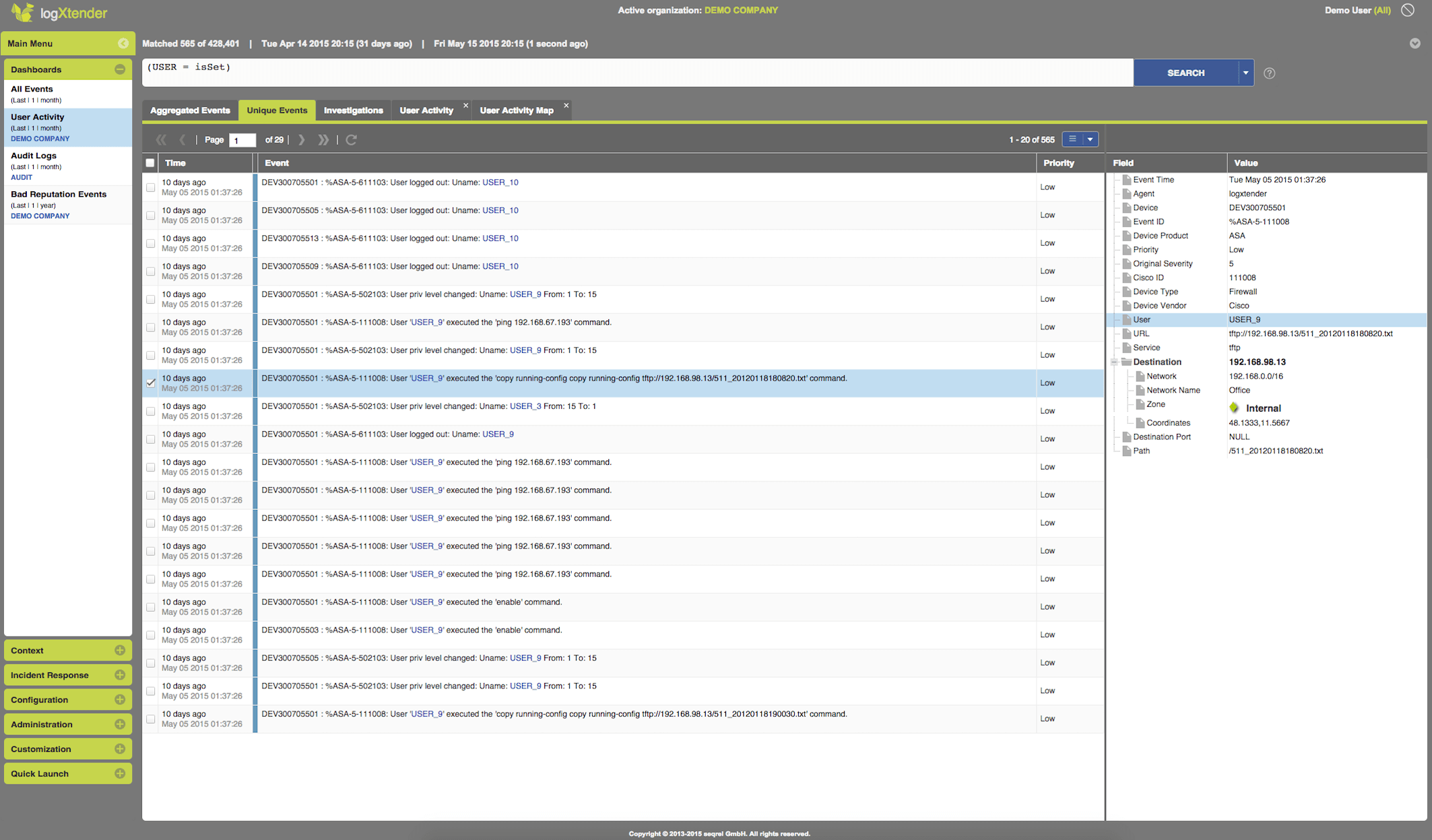
Role Based Data Privacy
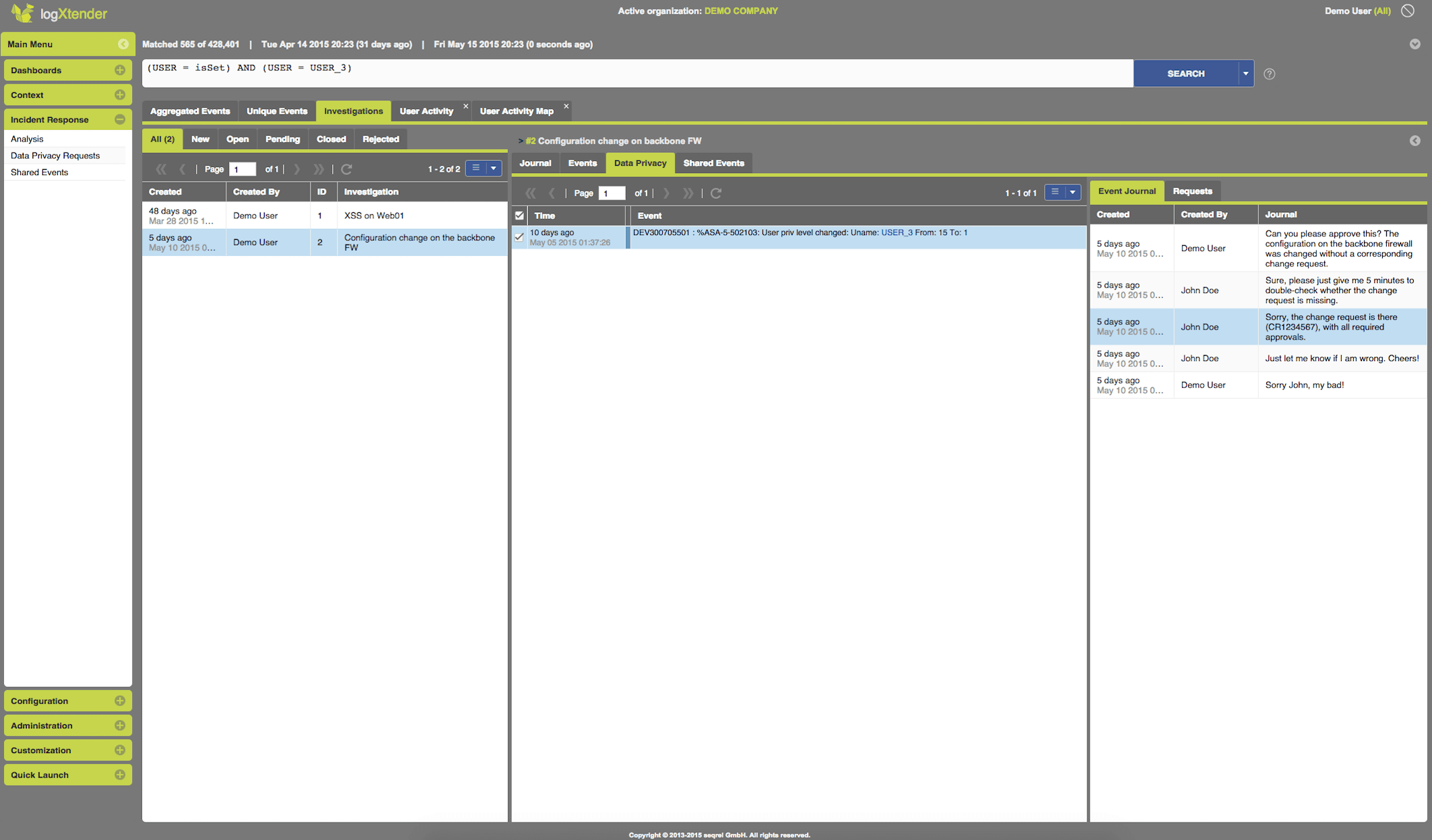
Data Privacy Workflow

Collaborative Incident Response

IPv6, Cloud-Ready, Multi-Tenant Architecture
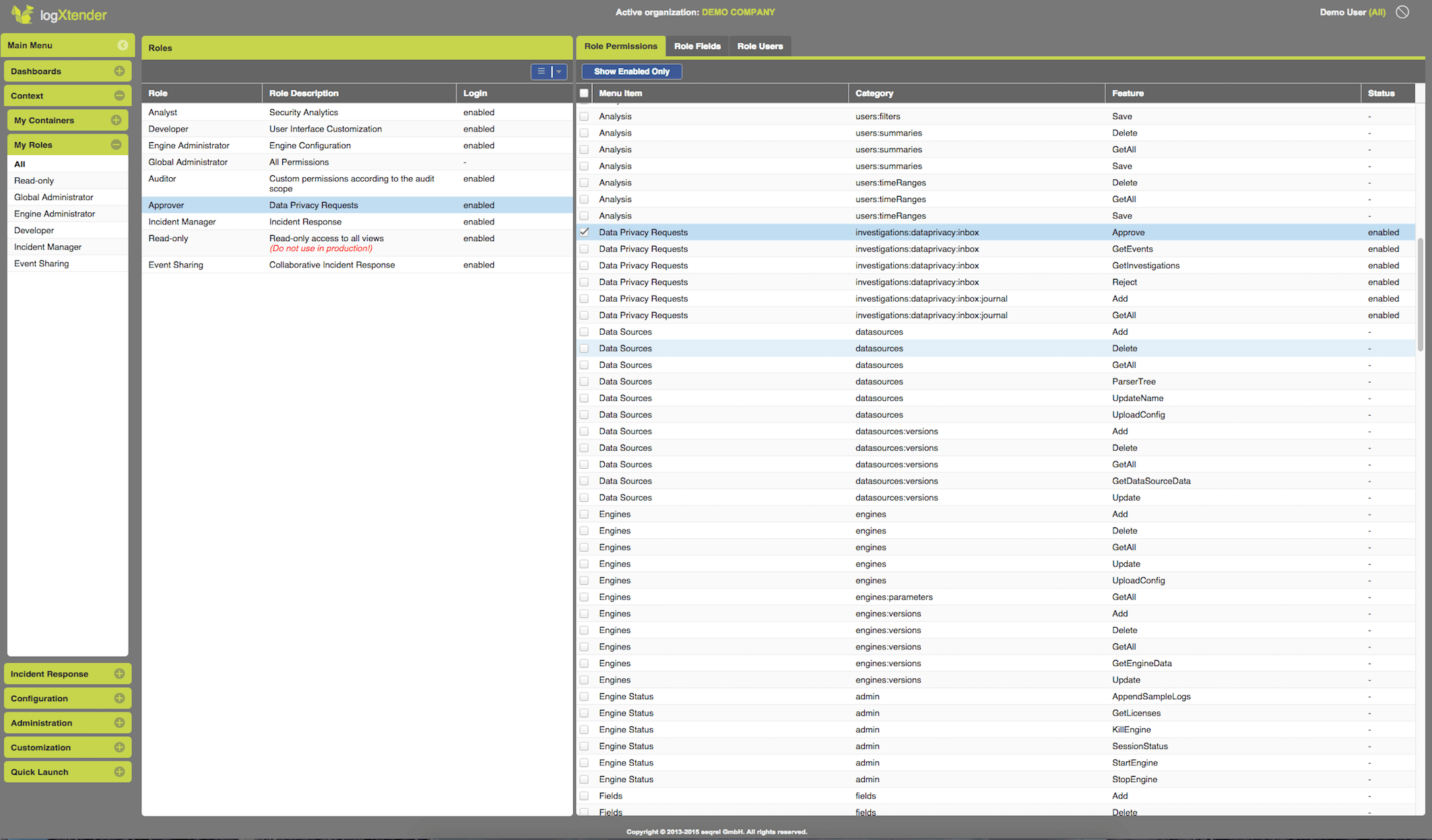
Granular Role Based Access Control
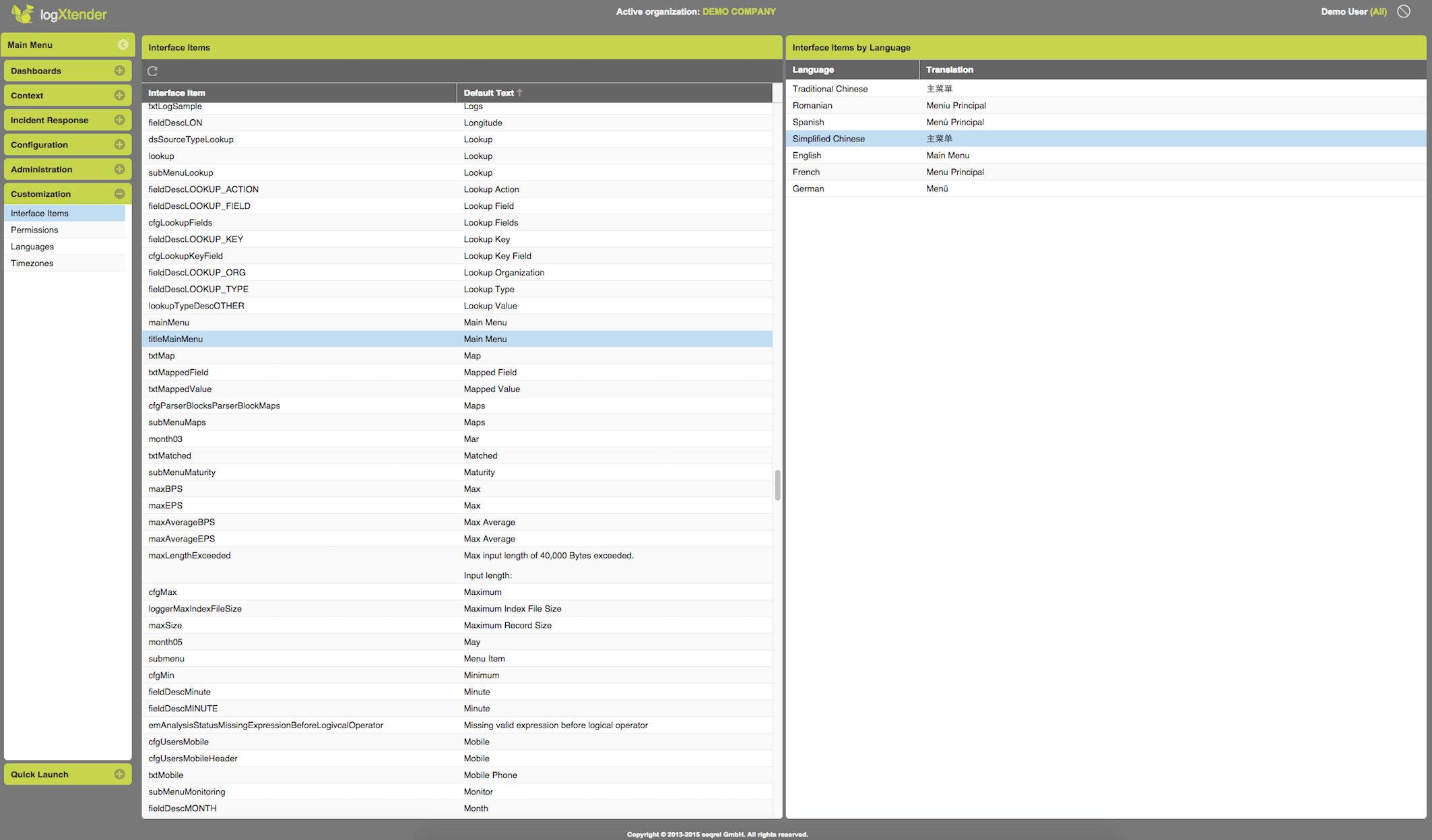
Customizable User Interface
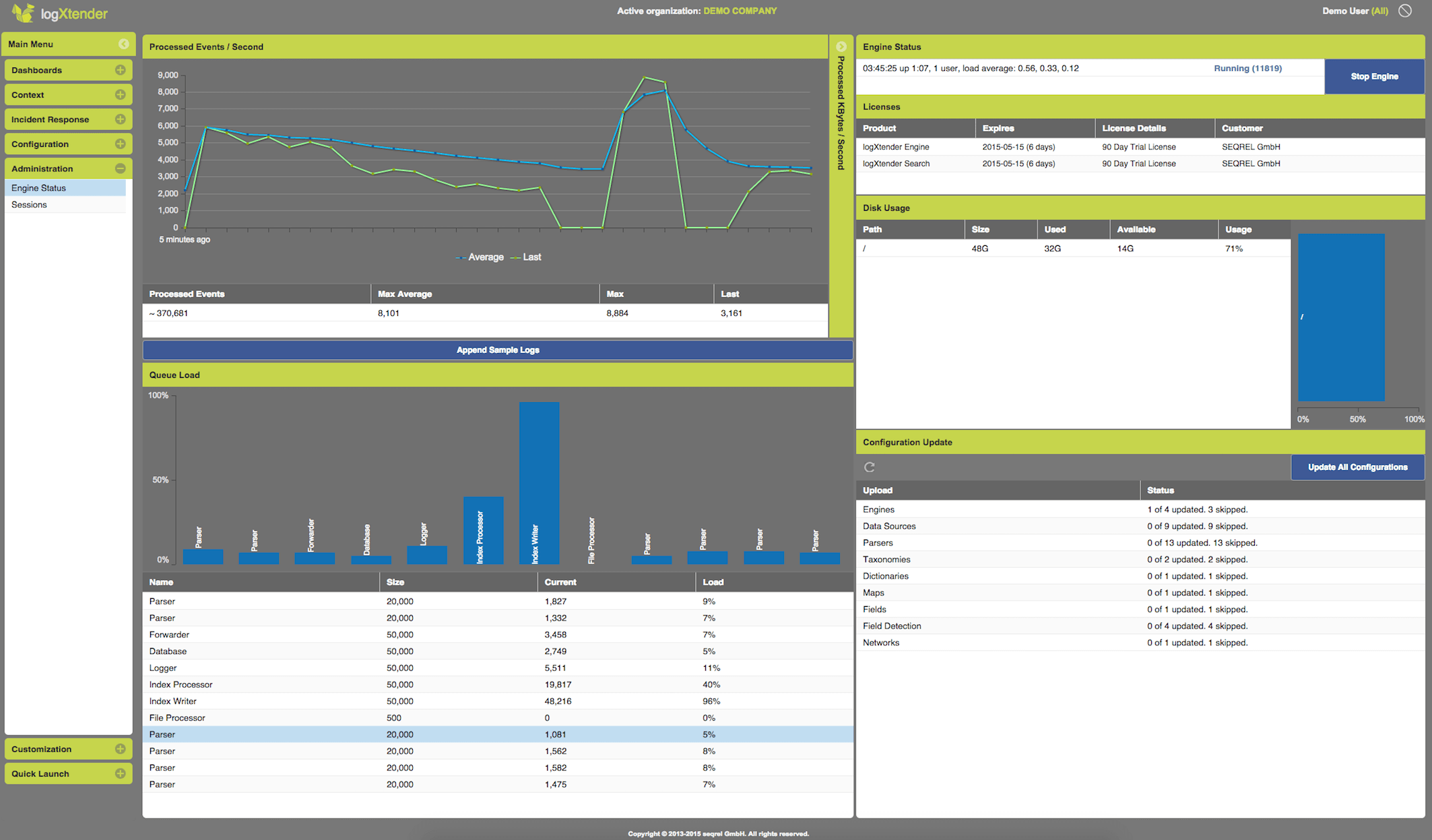
Multi-Threaded, Multi-Session, Multi-Tenant Architecture
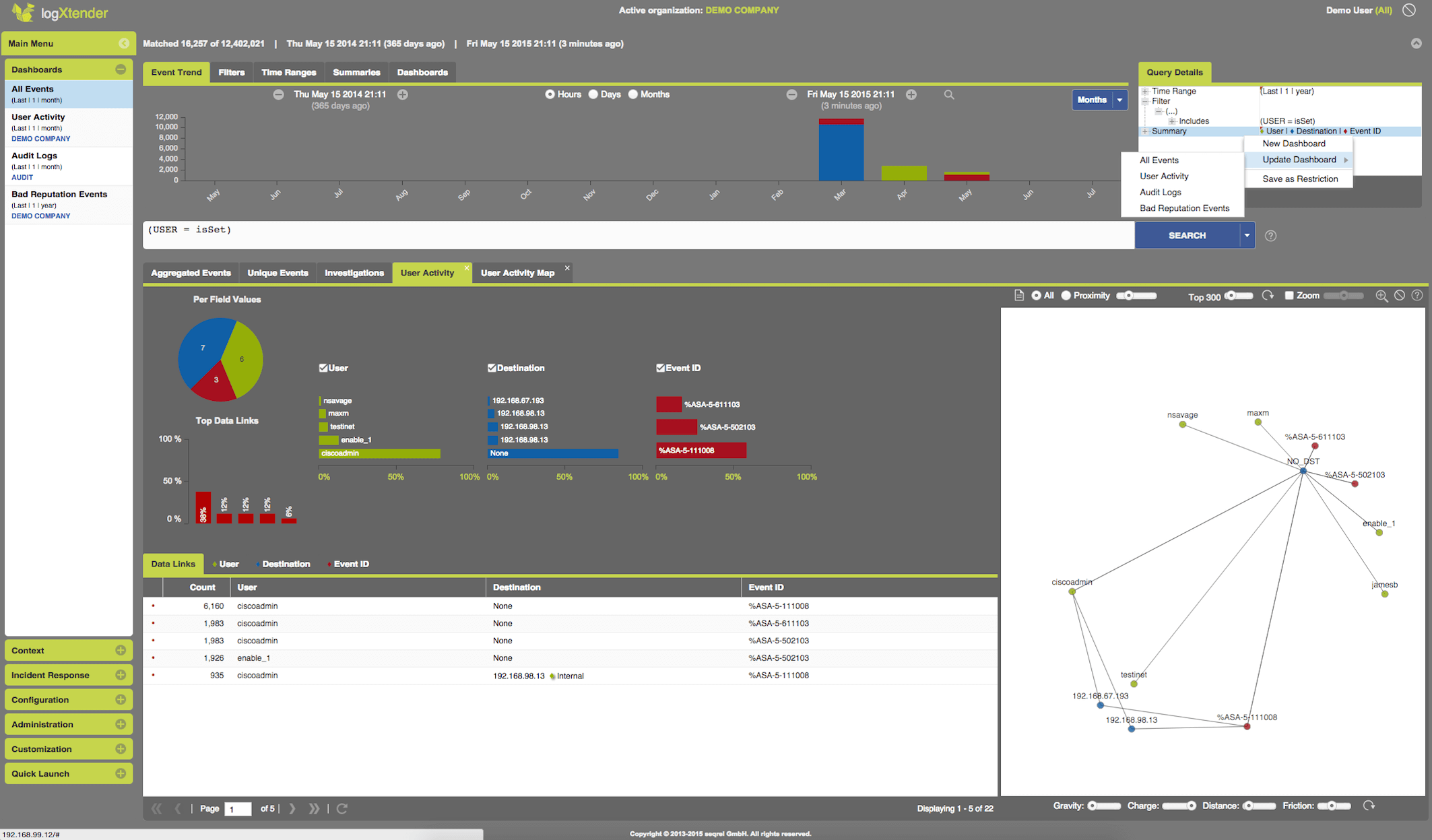
One-Click Data Analytics Dashboards
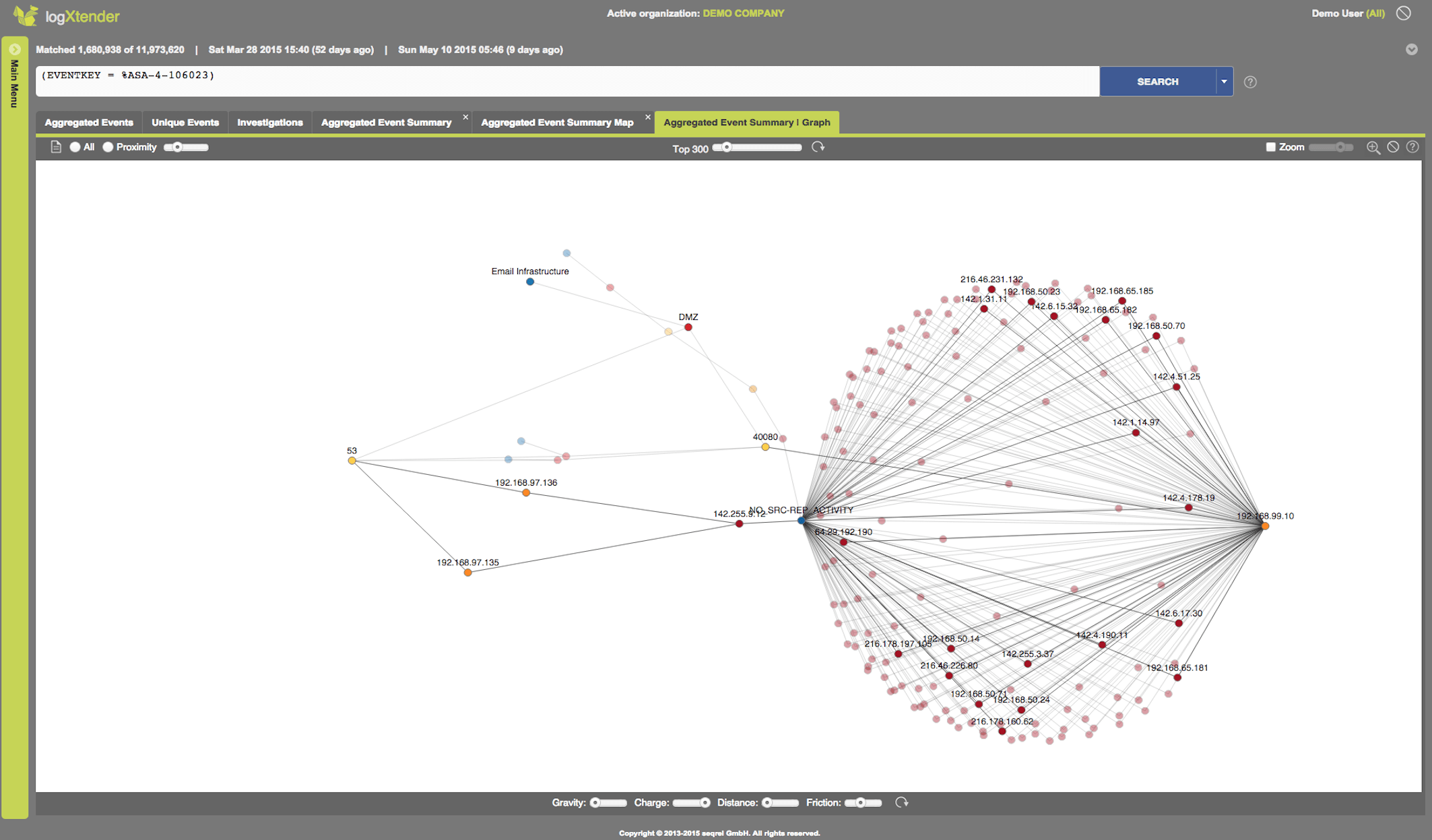
Enhanced Data Drilldown